Incident Response Plans in Healthcare: Can IRPs Be Automated?
By Mike Raia ![]() | Published May 10, 2016
| Published May 10, 2016
Under the HIPAA Breach Notification Interim Final Rule (PDF), healthcare organizations are required to document the investigation, incident risk analysis, and burden of proof following the discovery of a breach of unsecured protected health information. Accordingly, an Incident Response Plan (IRP) is essential for hospitals, and covered entities (and now their business associates under the HITEHC Act) to report security breaches and maintain compliance with the HIPAA Security Rule. An IRP is yet one more major endeavor for large healthcare organizations to not only embrace but to “do it right.” The consequences of an incomplete or disorganized IRP can be severe, with hefty fines for a HIPAA violation plus the cost of the security breach itself. So the question arises – once the IRP is fully defined and in place, can incident management be automated?
The answer is “yes.” Automating the entire process of the IRP is not only possible but encouraged. Automating the IRP allows a faster time-to-resolution while providing checks and balances for the process itself, ensuring nothing slips through the cracks. An automated IRP can also help prevent a security breach from doing major damage through its immediate response capabilities.
Defining or Evaluating an Effective Incident Response Plan (IRP)
 The first step is defining or evaluating an IRP is to dissect the people, processes, and data needs of your particular organization. There is no single, perfect way to design or implement an IRP, as the components of the incident response plan depend upon the people and workflows of the hospital or healthcare entity, which can vary greatly among various organizations. In addition, while you may already have an IRP in place, note that it should be a living document, being constantly tweaked as new information, processes, and IT equipment are added to the organization. Here are three areas to pay attention to when defining and evaluating your IRP.
The first step is defining or evaluating an IRP is to dissect the people, processes, and data needs of your particular organization. There is no single, perfect way to design or implement an IRP, as the components of the incident response plan depend upon the people and workflows of the hospital or healthcare entity, which can vary greatly among various organizations. In addition, while you may already have an IRP in place, note that it should be a living document, being constantly tweaked as new information, processes, and IT equipment are added to the organization. Here are three areas to pay attention to when defining and evaluating your IRP.
People
Define the roles of each person handling patient data, including doctors, nurses, billing and administrative personnel, insurance agents, IT personnel, outside vendors, contractors, and others. Collecting this data in advance will allow you to build a comprehensive IRP.
For non-data handling personnel, define security measurements such as educating users to prevent accidentally clicking on a link within a phishing email, for example.
Processes
Define the workflow processes that occur on a daily basis for each of the above personnel. When a data breach occurs, it interrupts one or more workflow processes that can allow it to be detected early. Defining and adhering to those workflows will provide a more efficient IRP. Examples of workflows include: When a patient enters the ER, what is the process for admission? For diagnosing? For discharging? Who inputs information into the system and how is it protected?
Data
The Department of Health and Human Services defines ‘‘data in motion’’ to include data that is moving through a network, including wireless transmission, whether by e-mail or structured electronic interchange. ‘‘Data at rest’’ includes data that resides in databases, file systems, flash drives, memory, and any other structured storage method. ‘‘Data in use’’ includes data in the process of being created, retrieved, updated, or deleted. ‘‘Data disposed of’’ includes discarded paper records or recycled electronic media.
This step is for your IT department: Follow the data through your own system and define hardware and software components that should be included in your IRP. This can include firewalls, servers, traffic monitoring devices, sandboxing, and other equipment that sees, stores, or captures your data.
Automating Your Incident Response
Once your IRP is in place, a far more efficient process is to automate the incident response plan using workflow tools. The “telephone game” wherein the first responder calls the IT department, who escalates to the security team, who escalates to the C-Suite, who escalates to the PR team for media triage, is not efficient when the stakes are this high.
The graphic below is a simplified view of how automation works for an IRP.
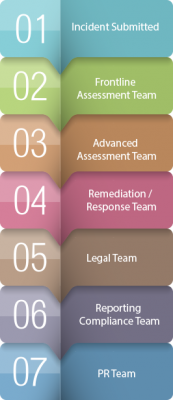
In Step 1, the incident is submitted. In most industries, this is usually handled by the IT department, who either notices that something is amiss, or is notified by the user that something has happened – perhaps a server has crashed, or a user clicked on a suspicious email which then took over their machine. But in healthcare, with data being input, and controlled by, many different people (doctors, nurses, administration staff) the power of automation is that the individual can “sound the alarm” by quickly alerting the frontline assessment team of a potential breach.
Why Automate?
According to Verizon’s 2016 Data Breach Investigations Report, the number of ransomware attacks has increased, with phishing attacks and malware still among the favorites of hackers to break into a network. These types of attacks are not always discovered by IT, as they are often found by the people handling the data. Consider a ransomware attack where a hacker may get into the network through a phishing email scam. A user clicks on the infected link, and malware is deposited. That malware then encrypts the hospital’s PHI (protected healthcare information) and sends a ransom note for the healthcare organization to deposit a large sum of money (typically via BitCoin) in order to receive the decryption key. In such a scenario, the breach could have been reported by the person who clicked on the link in the first place. He or she could have noticed, after the fact, that the link wasn’t going to where it originally indicated and, having been trained to look out for such things, could simply click on the first button “Incident Detected,” thus starting the chain of events for the investigation of the phishing scam and its potential damage.
In another scenario, consider the doctor who brings up his or her patient’s data in order to prescribe medication, only to find that the data is “gobbly gook” (encrypted). In the upper right-hand corner of the screen, that doctor also clicks “Incident Detected,” which again starts the IRP in motion – immediately.
In such cases, with immediate action, the automated IRP can actually prevent a breach from doing major damage. We live in an age of “see something, say something,” a term coined after 911 that empowers people to be the eyes and ears of law enforcement. An automated IRP brings this term alive when defending against a healthcare organization’s critical infrastructure. Automating your IRP using Integrify allows you to easily add an incident response system that's available to all employees 24X7 from one central location. To learn more, request a demo of Integrify.
Tags
healthcare it security
Categories
Industry Focus News

Mike Raia
Marketing the world's best workflow automation software and drinking way too much coffee. https://about.me/mikeraia