Access Control Management
Access control management policies can be easily enforced and implemented with workflow automation software
Access Control Management Is More Critical Than Ever
Maintaining information and system security can be difficult, especially as organizations grow personnel and systems. Managing who has access to which applications, folders, networks, modules, services, locations, etc., in other words, access control, can be a fundamental challenge for IT and security teams.
Enforcing access control policies is made significantly easier with workflow management tools like access control systems. When using a powerful access management system, user access authorization requests can be granted or refused in a standardized, repeatable way across the entire organization.
Developing Access Management Policies and Procedures
Properly safeguarding information and data within an organization is a core management responsibility. With so many systems handling information related to finance, personal information, and intellectual property within your organization, the risks of improper access and poor data security are authentic.
Management needs to develop sound, repeatable policies for dealing with those who have access to critical information. This means defining:
- The procedure by which someone requests and receives access.
- The rules (or models) that determine if that individual receives access.
- The rules governing the expiration of access.
Access Management Example: Integrating Access Control with Employee Onboarding/Offboarding
By making access control procedures part of the employee onboarding and offboarding process, a consistent method for handling the bulk of access requests can be more efficient.
During the onboarding process, new employees can request access to the majority of the systems, locations, etc., that they'll need all at once, along with requesting whatever hardware, software, devices, etc., they'll need to perform their role. This can reduce the ad-hoc requests that need to be handled throughout their employment. Of course, these ad-hoc requests can still be made through the system as needed.
Perhaps more importantly, employees going through an offboarding process can have their access and credentials quickly and reliably deactivated. Because the access management system is aware of all the access granted to the employee, the responsible administrators can check off as each access point is removed. This dramatically reduces the threat of unauthorized access and security issues created by a disgruntled former employee.
How Does the User Access Request Process Work?
Below is one access control example demonstrating a user access request process. We provide this process as a downloadable process app which illustrates, at a basic level, how an access request system could be designed.
This sample process allows a user to request access to software and systems. The form includes questions about the user and the type of access they need, including a separate form for any HR access needs. It provides two levels of approval with approver options for rejecting the request. It also allows for a delivery date to be submitted for each type of access.
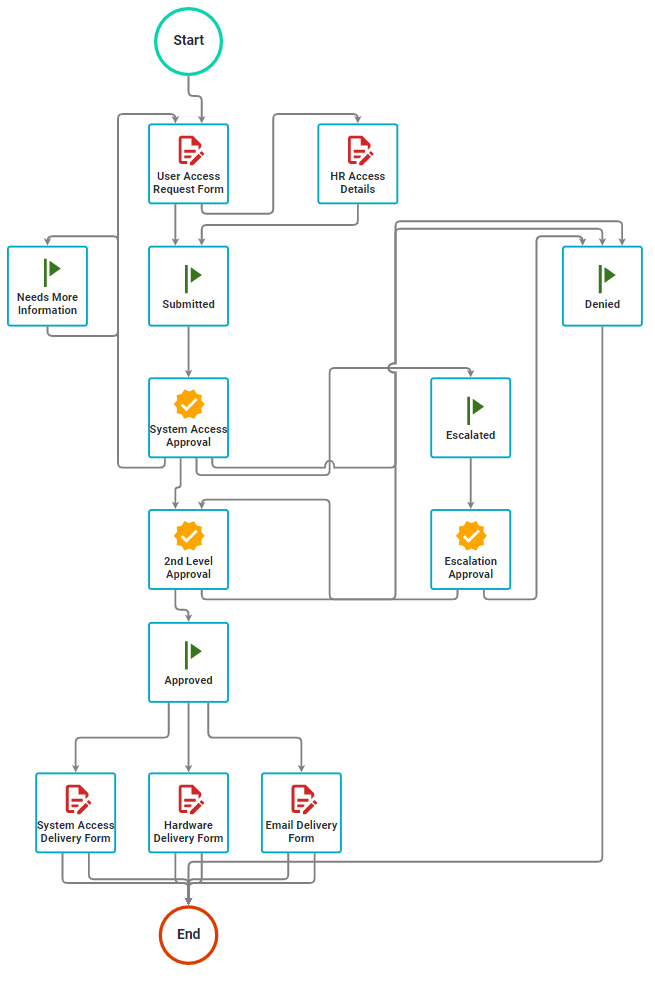
Notifications, alerts, and reminders ensure that tasks are performed within the expected timeframes. At the same time, escalations and delegations help prevent tasks from falling through the cracks. In addition, access requesters can always see the status of their requests without having to send emails or make phone calls. Allow users to make multiple access requests from one form to streamline the process. Route each request on the form differently, depending on the system or department.
Access Management Control Tools to Ensure Security and Compliance
Process Builder
Our visual process designer interface lets you design custom access request workflows using drag and drop. Automatically assign tasks and route information based on your organization's unique workflow. Set alerts, reminders, and escalations to keep work moving forward.
Form Designer
Easily create responsive, Web-based forms to capture access information. Include various field types, form logic, templates, and layouts to ensure the correct data is captured and routed.
Self-Service Portal
Provide a unified front-end experience that allows users to submit request forms, complete approvals, and track process status. Collaborate in real-time about work being performed. Provide visibility by role to see which tasks are completed, pending, or in progress for a great user experience.
Process Reporting
Track and maintain an audit trail of all your access request and approval workflows, including form data, users, and tasks performed. Follow team progress and use KPI scoreboards to track the overall efficiency and drive improvements. Build custom reports to analyze and share with stakeholders.
Process Integration (API)
Create workflow applications with process integration into existing enterprise systems. Our open architecture and standalone web service allow other applications to initiate a workflow, complete a list of tasks, update process statuses, and conduct other bi-directional activities. Connect everything with Integrify.
But Wait, There's More!
Managing access requests, while critical, is only one of the many use cases for workflow automation. Integrify clients have built various automated processes for Finance, HR, Operations, Marketing, Customer Service, and other business areas. For more information, visit our Solutions area.
Interested in Automating Your Access Management System or Other Workflow?
We have a variety of resources to help you on your journey to an automated workflow.

Automate Your Access Control Process
To see how quickly you can begin automating your access control processes, request a demonstration or trial of Integrify.

